Operational Technology Cybersecurity
Changing Threat Landscape or Simply Increased Awareness?
Cybersecurity seems to be in the news every day, whether it’s a new incident reported or new guidelines and regulations. Have cyberthreats increased, or are we simply becoming more aware of the risks?
Be the first to know
Subscribe to receive our Water Insights
The past 18 months have brought a significant focus on cybersecurity, particularly operational technology cybersecurity for critical infrastructure sectors such as water and wastewater. We’ve witnessed incidents, including breaches at the Oldsmar Florida Water Treatment Plant, Limestone Wastewater Treatment Plant (Maine), Colonial Pipeline and JBS (meat processing facilities). As a result of the recent Ukraine crisis, U.S. critical infrastructure owners have received several alerts from federal agencies requesting that they operate in a heightened sense of awareness and prepare for an event from Russian or Russian-sponsored sources, including notifications from Cybersecurity & Infrastructure Security Agency’s Shields Up, Water Information Sharing and Analysis Center (WaterISAC) Alerts and U.S. Environmental Protection Agency guidelines for water and wastewater operators.
After the U.S. Senate’s recent passage of the Strengthening American Cybersecurity Act, all critical infrastructure operators could soon face regulation requiring reporting of cybersecurity incidents to the federal government within 72 hours and certain information sharing to improve coordination of federal agencies if also passed by the House and signed into law. While specific threats have triggered the increased communications and heightened our sense of awareness, the risk has always been real. Although the reporting and communication requirements may increase, the potential consequences of a cybersecurity incident on critical infrastructure systems remain the same and may include both IT systems and OT production systems.
It is very difficult to quantify the likelihood of an event on a specific system or utility. The increasing number of known vulnerabilities for OT systems published by CISA is a concern, since these systems are utilized across market sectors worldwide and previous attacks like “Not Petya” have shown that a specific threat can spread to systems across the globe. The America’s Water Infrastructure Act was a step in the right direction toward recognition of cybersecurity as a threat to the resilience of U.S. water infrastructure. The inclusion of a requirement to assess cybersecurity recognizes that modern threat vectors might come from sources without direct physical access to the utility.
For many utilities, completion of the Water Act Assessment was faced with challenges related to resources, funding, scheduling and the pandemic. These challenges resulted in varying depth and breadth of the cybersecurity portion of the assessment and its resultant risk mitigation planning. Cybersecurity risk is similar to other risks faced by utilities where risk management begins with risk recognition and planning. Cybersecurity professionals continue to preach “when” not “if” there is a cyber event and that we cannot wait for an epoch before taking action.
Key questions to ask when determining risk tolerance include:
- How long can your utility run without your control system?
- If your process cannot be run without a control system, are there other mitigations available (water storage in distribution, wastewater storage ability, cross-connects), and how long are they sustainable?
- Have critical control system and process assets been identified and prioritized?
- If you had to restore control system assets, could you do it?
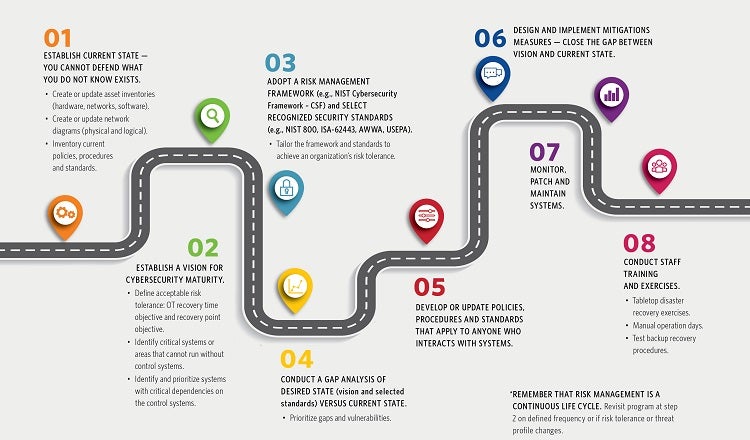
Well-formed cybersecurity programs are designed to achieve acceptable risk tolerance but cannot eliminate all risks. Management support for the cybersecurity program is critical to success. A roadmap to developing cybersecurity maturity is like master planning:
While cybersecurity risks and mitigations can feel overwhelming, it is important to remember that Defense in Depth, including people, processes and technologies, is widely accepted as a best practice for cybersecurity. Cybersecurity programs that address these key areas and establish an organization-wide culture of cybersecurity are well positioned to protect, detect, deter, respond and recover.
Finally, start somewhere. Anything that a utility can do today to lower their risk profile from yesterday is a step in the right direction. Even while starting a comprehensive cybersecurity program, it is common to start with protecting the network boundary (any connections to/from other systems) that represent potential entry points to the network. Additionally, I recommend verifying that the system backups for all devices and software are maintained both online and offline and have been tested to verify validity before an event. All utilities face this challenge together; I highly encourage everyone to continue the conversation by sharing best practices and lessons learned with your peers so that we may all improve together.